This year's final Teknisk informationssäkerhet course welcomed no less than four guest lecturers.
Lars Johansson stressed the importance of randomness when implementing cryptography.
Michael Westlund introduced the concept ot Digital Self-Defense and reminded us not to reuse passwords.
Tomas Karlsson revealed how seemingly independent agile teams can be subtly infiltrated by influencing their 'definition of done'.
And Åke Ljungqvist emphasised how a tested recovery plan can save tears as well as money.
(some of) my events
- 2025-05-19--20 Riskbaserat arbetssätt (teaching course, Stockholm)
- 2025-05-09 Certifierad IT-arkitekt (guest lecturing, Stockholm)
- 2025-04-02 Ownership and accessibility of art (attending seminar, Stockholm)
- 2025-03-31--05-30 AI Ethics for Engineers (taking course, Örebro University)
- 2024-03-21--05-31 Teoribildning inom riskhantering (taking course, Karlstad University)
2017-12-09
2017-11-11
InfoSec for IT Architects
DF Kompetens has a prestigious twelve-day curriculum for IT Architects which has certified 1200+ students by now. I was privileged to guest lecture half a day about Information Security.
This was the first time we did my group exercise in identifying and categorising Security Mechanisms with generalist students - as opposed to InfoSec pros. We learned that every technical mechanism has a process aspect.
Modern IT Architects have a holistic view where tech is just an ingredient, albeit important.
This was the first time we did my group exercise in identifying and categorising Security Mechanisms with generalist students - as opposed to InfoSec pros. We learned that every technical mechanism has a process aspect.
Modern IT Architects have a holistic view where tech is just an ingredient, albeit important.
2017-11-01
from craft to engineering
Security Architecture implies plurality.
In our recent Operativ InfoSec course, my eminent colleague Sebastian Åkerman talked about nomenclature and a systemic approach with a toolbox of Security Mechanisms. If an organisation can agree on terminology, it can describe existing capabilities (as well as desired ones) with bidirectional traceability between business need and component.
When InfoSec deals with building systems one at a time, architecture can help security work mature from craft to engineering.
2017-10-14
on the contested Digital Domain
When something concerns information as well as security, is it a matter of Information Security?
In our recent Strategisk Infosec course, I had the privilege to introduce a new chapter with guest lecturer Patrik Thunholm who gave a conceptual introduction to Influence Operations and Security Psychology.
Given the rapid digitisation, the Digital Domain is bound to become contested by various parties with an agenda. How can an organisation defend itself and how does this relate to classic InfoSec?
2017-09-27
on requirements in Stockholm
Security Requirements (SR) is not a trivial domain. ("Svårt", according to this word cloud.)
One might be tempted to go consult the nearest expert. And that is part of problem. Because SR concern so many of us. Either we write them (or should be writing them), or we're part of their target audience. Or, we should at least be aware of SR for other reasons.
This is pretty much what my seminar "KRAV-märkt" is about and 5 September I was privileged to host a SR breakfast at DF Kompetens in Stockholm.
2017-08-26
To Deceive and Mislead
Far from new, this idea is gaining traction in the social media era where source criticism is scarce and many "useful idiots" stand ready to share content with a thoughtless click. This is fertile ground for those who want to influence for reasons of politics, ideology or profit.
Starting next week, To Deceive and Mislead is a course I'm looking forward to. I'm particularly interested in the intersection between InfoWar and InfoSec.
2017-07-27
lessons from Överhogdal
Imagery from Wikimedia Commons (link)
In a store-shed by Överhogdal church, artist Paul Jonze made a stunning discovery in 1910. Laying like a large rug on the floor was a long-forgotten tapestry.
This textile treasure has been dated to the Viking Age and is by far the crown jewel of the county museum Jamtli where I've been privileged to experience it several times.
Textile artwork is certainly not my speciality but the Överhogdal tapestries are a great illustration of the challenges in preserving information. Archiving 101, if you will.
marveling at the Viking Age Överhogdal tapestries in stunningly good shape, we know not what they say. the medium is not the message. #gnite pic.twitter.com/y2BYzCsuNg— per stromsjo (@stromsjo) July 26, 2017
2017-07-06
ten years on Twitter
So, today it's been ten years.
I've learned so much there, built a network, found inspiration.
Most of the magic is gone, but for lack of a viable alternative I will be hanging on. Will you?
I recall the feeling when Twitter was new. Open, global dialogue. As a user, I was in control. There were no curating algorithms adding unwanted content - promoted tweets, "while you were away" and such nonsense. My feed was mine, simple as that. I'd be happy to pay for a subscription and get rid of the noise. Would you?collecting those pixels— per stromsjo (@stromsjo) July 6, 2007
I've learned so much there, built a network, found inspiration.
Most of the magic is gone, but for lack of a viable alternative I will be hanging on. Will you?
2017-06-02
on standards in Sollentuna
Ever wondered where standards (such as the ISO 27000) come from? Guess what? Somebody has to devise, write, publish and maintain them!
That's what technical committees are for. Standards are a global matter and I'm honoured to be part of (Technical Committee) TK318 of the non-profit association Swedish Standards Institute.
During our Spring meeting in summery Sollentuna, the discussion ranged from incidents and privacy to promoting standards. Good to be joining this team of national Infosec authorities.
That's what technical committees are for. Standards are a global matter and I'm honoured to be part of (Technical Committee) TK318 of the non-profit association Swedish Standards Institute.
During our Spring meeting in summery Sollentuna, the discussion ranged from incidents and privacy to promoting standards. Good to be joining this team of national Infosec authorities.
2017-05-26
on requirements in Umeå
To end five hectic days of teaching, I gave an updated version of my "KRAV-märkt" talk on Security Requirements as a lunch seminar at Umeå University together with Omegapoint colleagues.
The audience made a word cloud about Security Req's ("necessary" was the #1 word) and ranked the relative importance of tactics against modern threats (prevention was #1).
The salad was fine and there were plenty of good questions, not least about upcoming regulations in the privacy domain.
My thanks to everyone!
The audience made a word cloud about Security Req's ("necessary" was the #1 word) and ranked the relative importance of tactics against modern threats (prevention was #1).
The salad was fine and there were plenty of good questions, not least about upcoming regulations in the privacy domain.
My thanks to everyone!
2017-05-25
on capabilities in Östersund
I was honoured to give a guest lecture in Östersund at the Mid Sweden University Political Science course Policy-Making During Crises in Society.
Giving a practitioner's view on InfoSec and Continuity Risk, I chose to focus on key capabilities for organisations in dealing with a crisis.
We did a team exercise on creating pandemic plans for a fictitious restaurant, which turned out not to be much of a challenge for these security managers of the future.
A pleasure meeting Evangelia Petridou and her students!
Giving a practitioner's view on InfoSec and Continuity Risk, I chose to focus on key capabilities for organisations in dealing with a crisis.
We did a team exercise on creating pandemic plans for a fictitious restaurant, which turned out not to be much of a challenge for these security managers of the future.
A pleasure meeting Evangelia Petridou and her students!
2017-05-24
on archiving and agility
I was glad to see last week's Technical Infosec course fully booked.
This time I added a session on backup and archiving. Availability from a preservation perspective is becoming increasingly important as archives are being digitised.
We did a "100 points" Mentimeter exercise, ranking the relative importance of Agile Principles. The question was, which principles will have the most impact (positive or negative) on security work? Not surprisingly, principle #2 "Welcome changing requirements..." ended up on top.
This time I added a session on backup and archiving. Availability from a preservation perspective is becoming increasingly important as archives are being digitised.
We did a "100 points" Mentimeter exercise, ranking the relative importance of Agile Principles. The question was, which principles will have the most impact (positive or negative) on security work? Not surprisingly, principle #2 "Welcome changing requirements..." ended up on top.
2017-04-08
using smartphones in the classroom
In this week's course Operational Infosec, we experimented with Mentimeter. I had prepared a set of questions, and participants used their phones to answer.
They voted on how to spend resources among Software Security practices:
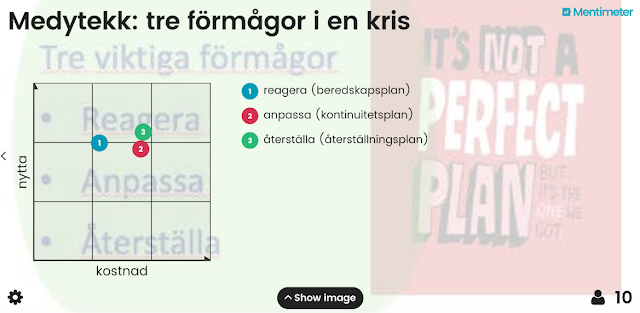
Also on the relative cost efficiency of three crisis capabilities for our fictitious company:
And finally on the relative importance of 12 privacy principles.
Mentimeter is intuitive. This was our first try and yet it only took five minutes from question to voting result.
They voted on how to spend resources among Software Security practices:
Also on the relative cost efficiency of three crisis capabilities for our fictitious company:
And finally on the relative importance of 12 privacy principles.
Mentimeter is intuitive. This was our first try and yet it only took five minutes from question to voting result.
2017-02-25
on the limitations of PPT
Building blocks of security are people, processes and technology ("PPT").
These days we rely more on technology than we used to.
Also, the amount of these ingredients will vary between organisations. Think of a highly regulated large entity, such as a bank, heavy in processes. Then think of a smaller company in another industry where no one ever talks about processes.
Why do some organisations seem to be doing well without adhering to this PPT scheme? What additional factor could help explain this?
These days we rely more on technology than we used to.
Also, the amount of these ingredients will vary between organisations. Think of a highly regulated large entity, such as a bank, heavy in processes. Then think of a smaller company in another industry where no one ever talks about processes.
Why do some organisations seem to be doing well without adhering to this PPT scheme? What additional factor could help explain this?
2017-02-18
the human element
Upholding security involves different levels in an organisation. This is reflected in the three courses I'm teaching - Strategic, Operational and Technical Infosec (see "my events" above).
But one factor is clearly missing on this "headline" level: people!
Strategies are devised by humans. Operational processes are designed by and populated with humans. And - without humans, technology won't help.
How can we approach the "human element" of Information Security? Trust and motivation will be key factors.
But one factor is clearly missing on this "headline" level: people!
Strategies are devised by humans. Operational processes are designed by and populated with humans. And - without humans, technology won't help.
How can we approach the "human element" of Information Security? Trust and motivation will be key factors.
Subscribe to:
Posts (Atom)
20250101